Linienzugbeeinflussung: Difference between revisions
en>Aaron-Tripel added Category:Railway signalling in Germany using HotCat |
|||
| Line 1: | Line 1: | ||
:''This article is about butterfly diagrams in FFT algorithms; for the sunspot diagrams of the same name, see [[Solar cycle]].'' | |||
[[Image:Butterfly-FFT.png|thumb|200px|right|[[Data flow diagram]] connecting the inputs ''x'' (left) to the outputs ''y'' that depend on them (right) for a "butterfly" step of a radix-2 Cooley–Tukey FFT. This diagram resembles a [[butterfly]] (as in the [[Morpho (butterfly)|Morpho butterfly]] shown for comparison), hence the name.]] In the context of [[fast Fourier transform]] algorithms, a '''butterfly''' is a portion of the computation that combines the results of smaller [[discrete Fourier transform]]s (DFTs) into a larger DFT, or vice versa (breaking a larger DFT up into subtransforms). The name "butterfly" comes from the shape of the data-flow diagram in the radix-2 case, as described below.<ref name=Oppenheim89>Alan V. Oppenheim, Ronald W. Schafer, and John R. Buck, ''Discrete-Time Signal Processing'', 2nd edition (Upper Saddle River, NJ: Prentice Hall, 1989)</ref> The same structure can also be found in the [[Viterbi algorithm]], used for finding the most likely sequence of hidden states. | |||
Most commonly, the term "butterfly" appears in the context of the [[Cooley–Tukey FFT algorithm]], which [[recursion|recursively]] breaks down a DFT of [[composite number|composite]] size ''n'' = ''rm'' into ''r'' smaller transforms of size ''m'' where ''r'' is the "radix" of the transform. These smaller DFTs are then combined via size-''r'' butterflies, which themselves are DFTs of size ''r'' (performed ''m'' times on corresponding outputs of the sub-transforms) pre-multiplied by [[root of unity|roots of unity]] (known as [[twiddle factor]]s). (This is the "decimation in time" case; one can also perform the steps in reverse, known as "decimation in frequency", where the butterflies come first and are post-multiplied by twiddle factors. See also the [[Cooley–Tukey FFT]] article.) | |||
==Radix-2 butterfly diagram== | |||
In the case of the radix-2 Cooley–Tukey algorithm, the butterfly is simply a DFT of size-2 that takes two inputs (''x''<sub>0</sub>, ''x''<sub>1</sub>) (corresponding outputs of the two sub-transforms) and gives two outputs (''y''<sub>0</sub>, ''y''<sub>1</sub>) by the formula (not including [[twiddle factor]]s): | |||
:<math>y_0 = x_0 + x_1 \, </math> | |||
:<math>y_1 = x_0 - x_1. \, </math> | |||
If one draws the data-flow diagram for this pair of operations, the (''x''<sub>0</sub>, ''x''<sub>1</sub>) to (''y''<sub>0</sub>, ''y''<sub>1</sub>) lines cross and resemble the wings of a [[butterfly]], hence the name (see also the illustration at right). | |||
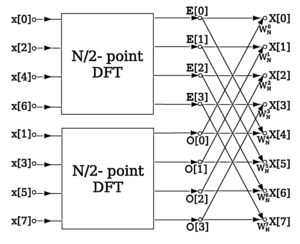
[[Image:DIT-FFT-butterfly.png|thumb|300px|right|A decimation-in-time radix-2 FFT breaks a length-''N'' DFT into two length-''N''/2 DFTs followed by a combining stage consisting of many butterfly operations.]] | |||
More specifically, a decimation-in-time FFT algorithm on ''n'' = 2<sup> ''p''</sup> inputs with respect to a primitive ''n''-th root of unity ''ω'' = exp(2''πi'' / ''n'') relies on O(''n'' log ''n'') butterflies of the form: | |||
:<math>y_0 = x_0 + x_1 \omega^k \, </math> | |||
:<math>y_1 = x_0 - x_1 \omega^k, \, </math> | |||
where ''k'' is an integer depending on the part of the transform being computed. Whereas the corresponding inverse transform can mathematically be performed by replacing ''ω'' with ''ω''<sup>−1</sup> (and possibly multiplying by an overall scale factor, depending on the normalization convention), one may also directly invert the butterflies: | |||
:<math>x_0 = \frac{1}{2} (y_0 + y_1) \, </math> | |||
:<math>x_1 = \frac{\omega^{-k}}{2} (y_0 - y_1), \, </math> | |||
corresponding to a decimation-in-frequency FFT algorithm. | |||
==Other uses== | |||
The butterfly can also be used to improve the randomness of large arrays of partially random numbers, by bringing every 32 or 64 bit word into causal contact with every other word through a desired hashing algorithm, so that a change in any one bit has the possibility of changing all the bits in the large array.<ref>*{{Citation | last1=Press | first1=WH | last2=Teukolsky | first2=SA | last3=Vetterling | first3=WT | last4=Flannery | first4=BP | year=2007 | title=Numerical Recipes: The Art of Scientific Computing | edition=3rd | publisher=Cambridge University Press | publication-place=New York | isbn=978-0-521-88068-8 | chapter=Section 7.2 Completely Hashing a Large Array | chapter-url=http://apps.nrbook.com/empanel/index.html#pg=358}}</ref> | |||
== See also == | |||
* [[Mathematical diagram]] | |||
* [[Zassenhaus lemma]] | |||
== References == | |||
<references/> | |||
==External links== | |||
* [http://www.relisoft.com/Science/Physics/fft.html explanation of the FFT and butterfly diagrams]. | |||
* [http://www.cmlab.csie.ntu.edu.tw/cml/dsp/training/coding/transform/fft.html butterfly diagrams of various FFT implementations (Radix-2, Radix-4, Split-Radix)]. | |||
<!-- dead link * [http://astron.berkeley.edu/~jrg/ngst/fft/fftbutfy.html explanation of butterfly diagrams specifically].--> | |||
[[Category:FFT algorithms]] | |||
[[Category:Diagrams]] | |||
Revision as of 19:20, 7 December 2013
- This article is about butterfly diagrams in FFT algorithms; for the sunspot diagrams of the same name, see Solar cycle.

In the context of fast Fourier transform algorithms, a butterfly is a portion of the computation that combines the results of smaller discrete Fourier transforms (DFTs) into a larger DFT, or vice versa (breaking a larger DFT up into subtransforms). The name "butterfly" comes from the shape of the data-flow diagram in the radix-2 case, as described below.[1] The same structure can also be found in the Viterbi algorithm, used for finding the most likely sequence of hidden states.
Most commonly, the term "butterfly" appears in the context of the Cooley–Tukey FFT algorithm, which recursively breaks down a DFT of composite size n = rm into r smaller transforms of size m where r is the "radix" of the transform. These smaller DFTs are then combined via size-r butterflies, which themselves are DFTs of size r (performed m times on corresponding outputs of the sub-transforms) pre-multiplied by roots of unity (known as twiddle factors). (This is the "decimation in time" case; one can also perform the steps in reverse, known as "decimation in frequency", where the butterflies come first and are post-multiplied by twiddle factors. See also the Cooley–Tukey FFT article.)
Radix-2 butterfly diagram
In the case of the radix-2 Cooley–Tukey algorithm, the butterfly is simply a DFT of size-2 that takes two inputs (x0, x1) (corresponding outputs of the two sub-transforms) and gives two outputs (y0, y1) by the formula (not including twiddle factors):
If one draws the data-flow diagram for this pair of operations, the (x0, x1) to (y0, y1) lines cross and resemble the wings of a butterfly, hence the name (see also the illustration at right).
More specifically, a decimation-in-time FFT algorithm on n = 2 p inputs with respect to a primitive n-th root of unity ω = exp(2πi / n) relies on O(n log n) butterflies of the form:
where k is an integer depending on the part of the transform being computed. Whereas the corresponding inverse transform can mathematically be performed by replacing ω with ω−1 (and possibly multiplying by an overall scale factor, depending on the normalization convention), one may also directly invert the butterflies:
corresponding to a decimation-in-frequency FFT algorithm.
Other uses
The butterfly can also be used to improve the randomness of large arrays of partially random numbers, by bringing every 32 or 64 bit word into causal contact with every other word through a desired hashing algorithm, so that a change in any one bit has the possibility of changing all the bits in the large array.[2]
See also
References
- ↑ Alan V. Oppenheim, Ronald W. Schafer, and John R. Buck, Discrete-Time Signal Processing, 2nd edition (Upper Saddle River, NJ: Prentice Hall, 1989)
- ↑ *Many property agents need to declare for the PIC grant in Singapore. However, not all of them know find out how to do the correct process for getting this PIC scheme from the IRAS. There are a number of steps that you need to do before your software can be approved.
Naturally, you will have to pay a safety deposit and that is usually one month rent for annually of the settlement. That is the place your good religion deposit will likely be taken into account and will kind part or all of your security deposit. Anticipate to have a proportionate amount deducted out of your deposit if something is discovered to be damaged if you move out. It's best to you'll want to test the inventory drawn up by the owner, which can detail all objects in the property and their condition. If you happen to fail to notice any harm not already mentioned within the inventory before transferring in, you danger having to pay for it yourself.
In case you are in search of an actual estate or Singapore property agent on-line, you simply should belief your intuition. It's because you do not know which agent is nice and which agent will not be. Carry out research on several brokers by looking out the internet. As soon as if you end up positive that a selected agent is dependable and reliable, you can choose to utilize his partnerise in finding you a home in Singapore. Most of the time, a property agent is taken into account to be good if he or she locations the contact data on his website. This may mean that the agent does not mind you calling them and asking them any questions relating to new properties in singapore in Singapore. After chatting with them you too can see them in their office after taking an appointment.
Have handed an trade examination i.e Widespread Examination for House Brokers (CEHA) or Actual Property Agency (REA) examination, or equal; Exclusive brokers are extra keen to share listing information thus making certain the widest doable coverage inside the real estate community via Multiple Listings and Networking. Accepting a severe provide is simpler since your agent is totally conscious of all advertising activity related with your property. This reduces your having to check with a number of agents for some other offers. Price control is easily achieved. Paint work in good restore-discuss with your Property Marketing consultant if main works are still to be done. Softening in residential property prices proceed, led by 2.8 per cent decline within the index for Remainder of Central Region
Once you place down the one per cent choice price to carry down a non-public property, it's important to accept its situation as it is whenever you move in – faulty air-con, choked rest room and all. Get round this by asking your agent to incorporate a ultimate inspection clause within the possibility-to-buy letter. HDB flat patrons routinely take pleasure in this security net. "There's a ultimate inspection of the property two days before the completion of all HDB transactions. If the air-con is defective, you can request the seller to repair it," says Kelvin.
15.6.1 As the agent is an intermediary, generally, as soon as the principal and third party are introduced right into a contractual relationship, the agent drops out of the image, subject to any problems with remuneration or indemnification that he could have against the principal, and extra exceptionally, against the third occasion. Generally, agents are entitled to be indemnified for all liabilities reasonably incurred within the execution of the brokers´ authority.
To achieve the very best outcomes, you must be always updated on market situations, including past transaction information and reliable projections. You could review and examine comparable homes that are currently available in the market, especially these which have been sold or not bought up to now six months. You'll be able to see a pattern of such report by clicking here It's essential to defend yourself in opposition to unscrupulous patrons. They are often very skilled in using highly unethical and manipulative techniques to try and lure you into a lure. That you must also protect your self, your loved ones, and personal belongings as you'll be serving many strangers in your home. Sign a listing itemizing of all of the objects provided by the proprietor, together with their situation. HSR Prime Recruiter 2010





