Cauchy's theorem (group theory): Difference between revisions
en>Gareth Griffith-Jones m Reverting revision by 75.36.159.189 identified as unconstructive ... using STiki ... your providing an edit summary might have helped to explain your intent. Clarification & Citation needed first. |
en>AxelBoldt m →Statement and proof: link |
||
| Line 1: | Line 1: | ||
In [[cryptography]], a '''cipher block chaining message authentication code''' ('''CBC-MAC''') is a technique for constructing a [[message authentication code]] from a [[block cipher]]. The message is encrypted with some block cipher algorithm in [[block cipher modes of operation|CBC mode]] to create a chain of blocks such that each block depends on the proper encryption of the previous block. This interdependence ensures that a change to any of the plaintext bits will cause the final encrypted block to change in a way that cannot be predicted or counteracted without knowing the key to the block cipher. | |||
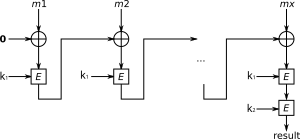
To calculate the CBC-MAC of message <math>m</math> one encrypts <math>m</math> in CBC mode with zero [[initialization vector]]. The following figure sketches the computation of the CBC-MAC of a message comprising blocks <math>m_1\|m_2\|\cdots\|m_x</math> using a secret key <math>k</math> and a block cipher <math>E</math>: | |||
[[Image:CBC-MAC structure (en).svg]] | |||
==Security with fixed and variable-length messages== | |||
If the block cipher used is secure (meaning that it is a [[pseudorandom permutation]]), then CBC-MAC is secure for fixed-length messages.<ref name="BKR">M. Bellare, J. Kilian and P. Rogaway. [http://www.cs.ucdavis.edu/research/tech-reports/1997/CSE-97-15.pdf The security of the cipher block chaining message authentication code.] JCSS 61(3):362–399, 2000.</ref> However, by itself, it is not secure for variable-length messages. Thus, any single key must only be used for messages of a fixed and known length. This is because an attacker who knows the correct message-tag (i.e. CBC-MAC) pairs for two messages <math>(m,</math> <math>t)</math> and <math>(m',</math> <math>t')</math> can generate a third message <math>m''</math> whose CBC-MAC will also be <math>t'</math>. This is simply done by XORing the first block of <math>m'</math> with <math>t</math> and then concatenating <math>m</math> with this modified <math>m'</math>; i.e., by making <math>m'' = m \| [(m_1' \oplus t) \| m_2' \| \dots \| m_x']</math>. When computing the MAC for the message <math>m''</math>, it follows that we compute the MAC for <math>m</math> in the usual manner as <math>t</math>, but when this value is chained forwards to the stage computing <math>E_{K_{MAC}}(m_1' \oplus t)</math> we will perform an exclusive OR operation with the value derived for the MAC of the first message. The presence of that tag in the new message means it will cancel, leaving no contribution to the MAC from the blocks of plain text in the first message <math>m</math>: <math>E_{K_{MAC}}(m_1' \oplus t \oplus t) = E_{K_{MAC}}(m_1')</math> and thus the tag for <math>m''</math> is <math>t'</math>. | |||
This problem cannot be solved by adding a message-size block to the end.<ref name=":0" /> There are three main ways of modifying CBC-MAC so that it is secure for variable length messages: 1) Input-length key separation; 2) Length-prepending; 3) Encrypt last block.<ref name=":0" /> In such a case, it may also be recommended to use a different mode of operation, for example, [[CMAC]] or [[HMAC]] to protect the integrity of variable-length messages. | |||
=== Length prepending === | |||
One solution is to include the length of the message in the first block;<ref>[http://www.iso.org/iso/iso_catalogue/catalogue_tc/catalogue_detail.htm?csnumber=30656 ISO/IEC 9797-1:1999 ''Information technology – Security techniques – Message Authentication Codes (MACs) – Part 1: Mechanisms using a block cipher''], clause 6.1.3 Padding Method 3</ref> in fact CBC-MAC has been proven secure as long as no two messages that are prefixes of each other are ever used and prepending the length is a special case of this.<ref name=":1">C. Rackoff and S. Gorbunov. On the Security of Block Chaining Message Authentication Code.</ref> This can be problematic if the message length may not be known when processing begins. | |||
=== Encrypt-last-block === | |||
Encrypt-last-block is defined as <math>\text{CBC-MAC-ELB}(m, (k_1, k_2)) = E(k_2, \text{CBC-MAC}(k_1, m))</math>.<ref name=":0">See Section 5 of Bellare, et al.</ref> Compared to the other discussed methods of extending CBC-MAC to variable-length messages, encrypt-last-block has the advantage of not needing to know the length of the message until the end of the computation. | |||
[[Image:CBC-MAC (encrypt last block) structure.svg|right|300px|thumb|Computation of CBC-MAC Encrypt-last-block.]] | |||
==Attack methods== | |||
As with many cryptographic schemes, naïve use of ciphers and other protocols may lead to attacks being possible, reducing the effectiveness of the cryptographic protection (or even rendering it useless). We present attacks which are possible due to using the CBC-MAC incorrectly. | |||
===Using the same key for encryption and authentication=== | |||
One common mistake is to reuse the same key <math>k</math> for CBC encryption and CBC-MAC. Although a reuse of a key for different purposes is a bad practice in general, in this particular case the mistake leads to a spectacular attack: | |||
Suppose Alice has sent to Bob the cipher text blocks <math>C = C_1\ ||\ C_2\ ||\ \dots\ ||\ C_n</math>. During the transmission process, Eve can tamper with any of the <math>C_1 , \dots , C_{n-1}</math> cipher-text blocks and adjust any of the bits therein as she chooses, provided that the final block, <math>C_n</math>, remains the same. We assume, for the purposes of this example and without loss of generality, that the initialisation vector used for the encryption process is a vector of zeroes. | |||
When Bob receives the message, he will first decrypt the message by reversing the encryption process which Alice applied, using the cipher text blocks <math>C=C_1\ ||\ C_2\ ||\ \cdots\ ||\ C_n</math>. During the transmission process, Eve can tamper with any of the <math>C_1 , \dots , C_{n-1}</math> cipher text blocks and adjust any of the bits therein as she chooses, provided that the final block, <math>C_n</math>, remains the same. Her tampered version, later delivered to Bob in replacement of Alice's original, is <math>C'=C_1'\ ||\ \dots\ ||\ C_{n-1}'\ ||\ C_n</math>. | |||
Bob first decrypts the message received using the shared secret key <math>K</math> to obtain corresponding plain text. Note that all plain text produced will be different from that which Alice originally sent, because Eve has modified all but the last cipher text block. In particular, the final plain text, <math>P_n'</math>, differs from the original, <math>P_n</math>, which Alice sent; although <math>C_n</math> is the same, <math>C_{n-1}' \not = C_{n-1}</math>, so a different plain text <math>P_n'</math> is produced when chaining the previous cipher text block into the exclusive-OR after decryption of <math>C_n</math>: <math>P_n' = C_{n-1}' \oplus E_K^{-1}(C_n)</math>. | |||
It follows that Bob will now compute the authentication tag using CBC-MAC over all the values of plain text which he decoded. The tag for the new message, <math>t'</math>, is given by: | |||
<math>t' = E_K(P_n' \oplus E_K(P_{n-1}' \oplus E_K( \dots \oplus E_K(P_1'))))</math> | |||
Notice that this expression is equal to | |||
<math>t' = E_K(P_n' \oplus C_{n-1}')</math> | |||
which is exactly <math>C_n</math>: | |||
<math>t' = E_K(C_{n-1}' \oplus E_K^{-1}(C_n) \oplus C_{n-1}') = E_K(E_K^{-1}(C_n)) = C_n</math> | |||
and it follows that <math>t' = C_n = t</math>. | |||
Therefore, Eve was able to modify the cipher text in transit (without necessarily knowing what plain text it corresponds to) such that an entirely different message, <math>P'</math>, was produced, but the tag for this message matched the tag of the original, and Bob was unaware that the contents had been modified in transit. By definition, a Message Authentication Code is ''broken'' if we can find a different message (a sequence of plain-text pairs <math>P'</math>) which produces the same tag as the previous message, <math>P</math>, with <math>P \not = P'</math>. It follows that the message authentication protocol, in this usage scenario, has been broken, and Bob has been deceived into believing Alice sent him a message which she did not produce. | |||
If, instead, we use different keys for the encryption and authentication stages, say <math>K_1</math> and <math>K_2</math>, respectively, this attack is foiled. The decryption of the modified cipher-text blocks <math>C_i'</math> obtains some plain text string <math>P_i'</math>. However, due to the MAC's usage of a different key <math>K_2</math>, we cannot "undo" the decryption process in the forward step of the computation of the message authentication code so as to produce the same tag; each modified <math>P_i'</math> will now be encrypted by <math>K_2</math> in the CBC-MAC process to some value <math>MAC_i \not = C_i'</math>. | |||
This example also shows that a CBC-MAC cannot be used as a collision resistant one-way function: given a key it is trivial to create a different message which "hashes" to the same tag. | |||
===Allowing the initialisation vector to vary in value=== | |||
When encrypting data using a block cipher in [[cipher block chaining]] (or another) mode, it is common to introduce an [[initialization vector]] to the first stage of the encryption process. It is typically required that this vector be chosen randomly (a [[nonce]]) and that it is not repeated for any given secret key under which the block cipher operates. This provides semantic security, by means of ensuring the same plain text is not encrypted to the same cipher text, allowing an attacker to infer a relationship exists. | |||
When computing a message authentication code, such as by CBC-MAC, the use of an initialisation vector is a possible attack vector. | |||
In the operation of a cipher block chaining cipher, the first block of plain text is mixed with the initialisation vector using an exclusive OR (<math>P_1 \oplus IV</math>). The result of this operation is the input to the block cipher for encryption. | |||
However, when performing encryption and decryption, we are required to send the initialisation vector in plain text - typically as the block immediately preceding the first block of cipher text - such that the first block of plain text can be decrypted and recovered successfully. If computing a MAC, we will also need to transmit the initialisation vector to the other party in plain text so that they can verify the tag on the message matches the value they have computed. | |||
If we allow the initialisation vector to be selected arbitrarily, it follows that the first block of plain text can potentially be modified (transmitting a different message) while producing the same message tag. | |||
Consider a message <math>M_1 = P_1 | P_2 | \dots</math>. In particular, when computing the message tab for CBC-MAC, suppose we choose an initialisation vector <math>IV_1</math> such that computation of the MAC begins with <math>E_K(IV_1 \oplus P_1)</math>. This produces a (message, tag) pair <math>(M_1, T_1)</math>. | |||
Now produce the message <math>M_2 = P_1' | P_2 | \dots</math>. For each bit modified in <math>P_1'</math>, flip the corresponding bit in the initialisation vector to produce the initialisation vector <math>IV_1'</math>. It follows that to compute the MAC for this message, we begin the computation by <math>E_K(P_1' \oplus IV_1')</math>. As bits in both the plain text and initialisation vector have been flipped in the same places, the modification is cancelled in this first stage, meaning the input to the block cipher is identical to that for <math>M_1</math>. If no further changes are made to the plain text, the same tag will be derived despite a different message being transmitted. | |||
If the freedom to select an initialisation vector is removed and all implementations of CBC-MAC fix themselves on a particular initialisation vector (often the vector of zeroes, but in theory, it could be anything provided all implementations agree), this attack cannot proceed. | |||
==Standards that define the algorithm== | |||
[[FIPS PUB 113]] ''Computer Data Authentication'' is a (now obsolete) [[Federal Information Processing Standard|U.S. government standard]] that specified the CBC-MAC algorithm using [[Data Encryption Standard|DES]] as the block cipher. | |||
The CBC-MAC algorithm is equivalent to [[ISO/IEC 9797-1]] MAC Algorithm 1. | |||
==See also== | |||
* [[CMAC]] – A block-cipher–based MAC algorithm which is secure for messages of different lengths (recommended by [[NIST]]). | |||
* [[One-key MAC|OMAC]] and [[PMAC (cryptography)|PMAC]] – Other methods to turn block ciphers into message authentication codes (MACs). | |||
* [[One-way compression function]] – Hash functions can be made from block ciphers. But note, there are significant differences in function and uses for security between [[Message authentication code|MACs]] (such as CBC-MAC) and [[Cryptographic hash function|hashes]]. | |||
== References == | |||
{{reflist}} | |||
{{Cryptography navbox | hash}} | |||
[[Category:Message authentication codes]] | |||
[[Category:Block cipher modes of operation]] | |||
Revision as of 18:25, 28 May 2013
In cryptography, a cipher block chaining message authentication code (CBC-MAC) is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a chain of blocks such that each block depends on the proper encryption of the previous block. This interdependence ensures that a change to any of the plaintext bits will cause the final encrypted block to change in a way that cannot be predicted or counteracted without knowing the key to the block cipher.
To calculate the CBC-MAC of message one encrypts in CBC mode with zero initialization vector. The following figure sketches the computation of the CBC-MAC of a message comprising blocks using a secret key and a block cipher :
Security with fixed and variable-length messages
If the block cipher used is secure (meaning that it is a pseudorandom permutation), then CBC-MAC is secure for fixed-length messages.[1] However, by itself, it is not secure for variable-length messages. Thus, any single key must only be used for messages of a fixed and known length. This is because an attacker who knows the correct message-tag (i.e. CBC-MAC) pairs for two messages and can generate a third message whose CBC-MAC will also be . This is simply done by XORing the first block of with and then concatenating with this modified ; i.e., by making . When computing the MAC for the message , it follows that we compute the MAC for in the usual manner as , but when this value is chained forwards to the stage computing we will perform an exclusive OR operation with the value derived for the MAC of the first message. The presence of that tag in the new message means it will cancel, leaving no contribution to the MAC from the blocks of plain text in the first message : and thus the tag for is .
This problem cannot be solved by adding a message-size block to the end.[2] There are three main ways of modifying CBC-MAC so that it is secure for variable length messages: 1) Input-length key separation; 2) Length-prepending; 3) Encrypt last block.[2] In such a case, it may also be recommended to use a different mode of operation, for example, CMAC or HMAC to protect the integrity of variable-length messages.
Length prepending
One solution is to include the length of the message in the first block;[3] in fact CBC-MAC has been proven secure as long as no two messages that are prefixes of each other are ever used and prepending the length is a special case of this.[4] This can be problematic if the message length may not be known when processing begins.
Encrypt-last-block
Encrypt-last-block is defined as .[2] Compared to the other discussed methods of extending CBC-MAC to variable-length messages, encrypt-last-block has the advantage of not needing to know the length of the message until the end of the computation.
Attack methods
As with many cryptographic schemes, naïve use of ciphers and other protocols may lead to attacks being possible, reducing the effectiveness of the cryptographic protection (or even rendering it useless). We present attacks which are possible due to using the CBC-MAC incorrectly.
Using the same key for encryption and authentication
One common mistake is to reuse the same key for CBC encryption and CBC-MAC. Although a reuse of a key for different purposes is a bad practice in general, in this particular case the mistake leads to a spectacular attack:
Suppose Alice has sent to Bob the cipher text blocks . During the transmission process, Eve can tamper with any of the cipher-text blocks and adjust any of the bits therein as she chooses, provided that the final block, , remains the same. We assume, for the purposes of this example and without loss of generality, that the initialisation vector used for the encryption process is a vector of zeroes.
When Bob receives the message, he will first decrypt the message by reversing the encryption process which Alice applied, using the cipher text blocks . During the transmission process, Eve can tamper with any of the cipher text blocks and adjust any of the bits therein as she chooses, provided that the final block, , remains the same. Her tampered version, later delivered to Bob in replacement of Alice's original, is .
Bob first decrypts the message received using the shared secret key to obtain corresponding plain text. Note that all plain text produced will be different from that which Alice originally sent, because Eve has modified all but the last cipher text block. In particular, the final plain text, , differs from the original, , which Alice sent; although is the same, , so a different plain text is produced when chaining the previous cipher text block into the exclusive-OR after decryption of : .
It follows that Bob will now compute the authentication tag using CBC-MAC over all the values of plain text which he decoded. The tag for the new message, , is given by:
Notice that this expression is equal to
Therefore, Eve was able to modify the cipher text in transit (without necessarily knowing what plain text it corresponds to) such that an entirely different message, , was produced, but the tag for this message matched the tag of the original, and Bob was unaware that the contents had been modified in transit. By definition, a Message Authentication Code is broken if we can find a different message (a sequence of plain-text pairs ) which produces the same tag as the previous message, , with . It follows that the message authentication protocol, in this usage scenario, has been broken, and Bob has been deceived into believing Alice sent him a message which she did not produce.
If, instead, we use different keys for the encryption and authentication stages, say and , respectively, this attack is foiled. The decryption of the modified cipher-text blocks obtains some plain text string . However, due to the MAC's usage of a different key , we cannot "undo" the decryption process in the forward step of the computation of the message authentication code so as to produce the same tag; each modified will now be encrypted by in the CBC-MAC process to some value .
This example also shows that a CBC-MAC cannot be used as a collision resistant one-way function: given a key it is trivial to create a different message which "hashes" to the same tag.
Allowing the initialisation vector to vary in value
When encrypting data using a block cipher in cipher block chaining (or another) mode, it is common to introduce an initialization vector to the first stage of the encryption process. It is typically required that this vector be chosen randomly (a nonce) and that it is not repeated for any given secret key under which the block cipher operates. This provides semantic security, by means of ensuring the same plain text is not encrypted to the same cipher text, allowing an attacker to infer a relationship exists.
When computing a message authentication code, such as by CBC-MAC, the use of an initialisation vector is a possible attack vector.
In the operation of a cipher block chaining cipher, the first block of plain text is mixed with the initialisation vector using an exclusive OR (). The result of this operation is the input to the block cipher for encryption.
However, when performing encryption and decryption, we are required to send the initialisation vector in plain text - typically as the block immediately preceding the first block of cipher text - such that the first block of plain text can be decrypted and recovered successfully. If computing a MAC, we will also need to transmit the initialisation vector to the other party in plain text so that they can verify the tag on the message matches the value they have computed.
If we allow the initialisation vector to be selected arbitrarily, it follows that the first block of plain text can potentially be modified (transmitting a different message) while producing the same message tag.
Consider a message . In particular, when computing the message tab for CBC-MAC, suppose we choose an initialisation vector such that computation of the MAC begins with . This produces a (message, tag) pair .
Now produce the message . For each bit modified in , flip the corresponding bit in the initialisation vector to produce the initialisation vector . It follows that to compute the MAC for this message, we begin the computation by . As bits in both the plain text and initialisation vector have been flipped in the same places, the modification is cancelled in this first stage, meaning the input to the block cipher is identical to that for . If no further changes are made to the plain text, the same tag will be derived despite a different message being transmitted.
If the freedom to select an initialisation vector is removed and all implementations of CBC-MAC fix themselves on a particular initialisation vector (often the vector of zeroes, but in theory, it could be anything provided all implementations agree), this attack cannot proceed.
Standards that define the algorithm
FIPS PUB 113 Computer Data Authentication is a (now obsolete) U.S. government standard that specified the CBC-MAC algorithm using DES as the block cipher.
The CBC-MAC algorithm is equivalent to ISO/IEC 9797-1 MAC Algorithm 1.
See also
- CMAC – A block-cipher–based MAC algorithm which is secure for messages of different lengths (recommended by NIST).
- OMAC and PMAC – Other methods to turn block ciphers into message authentication codes (MACs).
- One-way compression function – Hash functions can be made from block ciphers. But note, there are significant differences in function and uses for security between MACs (such as CBC-MAC) and hashes.
References
43 year old Petroleum Engineer Harry from Deep River, usually spends time with hobbies and interests like renting movies, property developers in singapore new condominium and vehicle racing. Constantly enjoys going to destinations like Camino Real de Tierra Adentro.
- ↑ M. Bellare, J. Kilian and P. Rogaway. The security of the cipher block chaining message authentication code. JCSS 61(3):362–399, 2000.
- ↑ 2.0 2.1 2.2 See Section 5 of Bellare, et al.
- ↑ ISO/IEC 9797-1:1999 Information technology – Security techniques – Message Authentication Codes (MACs) – Part 1: Mechanisms using a block cipher, clause 6.1.3 Padding Method 3
- ↑ C. Rackoff and S. Gorbunov. On the Security of Block Chaining Message Authentication Code.













![m''=m\|[(m_{1}'\oplus t)\|m_{2}'\|\dots \|m_{x}']](https://wikimedia.org/api/rest_v1/media/math/render/svg/d2359189c7c2c4e8e203758741488322c77d97a2)


































